[v10] Two-Factor Authentication (2FA)
The following shows the “Two-Factor Authentication (2FA)” tab under System Settings > Basic.
For newly installed AhsayCBS v10.1.0.0 and onwards, the Two-Factor Authentication that will be available will be the Mobile Authentication.
However for upgraded AhsayCBS with Twilio Credentials Verification setup, there will be two options available for two-factor authentication which are the following:
-
Mobile Authentication feature is introduced to provide two-factor authentication during log in for added security. During log in, aside from providing the normal Ahsay password, an additional step will need to be completed to finish the log in steps.
Users have two options once this feature is enabled to complete the log in:
- Accept the notification request sent to the Ahsay Mobile app or use a time-based one-time password code.
- Provide the time-based one-time password code generated by a third-party authenticator app. Examples of these apps are Google Authenticator, Microsoft Authenticator, LastPass Authenticator etc.
-
Twilio Credentials Verification
This option will only be available to legacy clients who are currently using Twilio Credentials Verification on AhsayCBS v8.3.0.30 to 8.3.6.x and have upgraded to AhsayCBS v10.1.0.0 or above. Users of Twilio Credentials Verification may continue using this on AhsayCBS v10.1.0.0 or above. After the upgrade, settings of Twilio Credentials Verification will be automatically migrated.
As Twilio Credentials Verification has been replaced with Mobile Authentication, for users who have not setup Twilio Credentials Verification in pre-AhsayCBS v10.1.0.0 versions, this option will not be available once you upgrade to AhsayCBS v10.1.0.0 or above.
For legacy Twilio clients, only one of the options for two-factor authentication may be enabled. It is not possible to enable both Mobile Authentication and Twilio Credentials Verification at the same time. Either continue using Twilio Credentials Verification or switch to Mobile Authentication.
Once the two-factor authentication switch to Mobile Authentication is confirmed, the Twilio Credentials Verification will be permanently deleted from AhsayCBS and you will no longer be able to re-enable this feature.
If the “Require Two-Factor Authentication for user logon” is enabled, on the next log in on all AhayOBM/AhsayACB v10.1.0.0 or above clients or AhsayCBS web console, the user will be required to register a mobile device for the new Mobile Authentication 2FA, otherwise they will not be allowed to proceed with the log in.
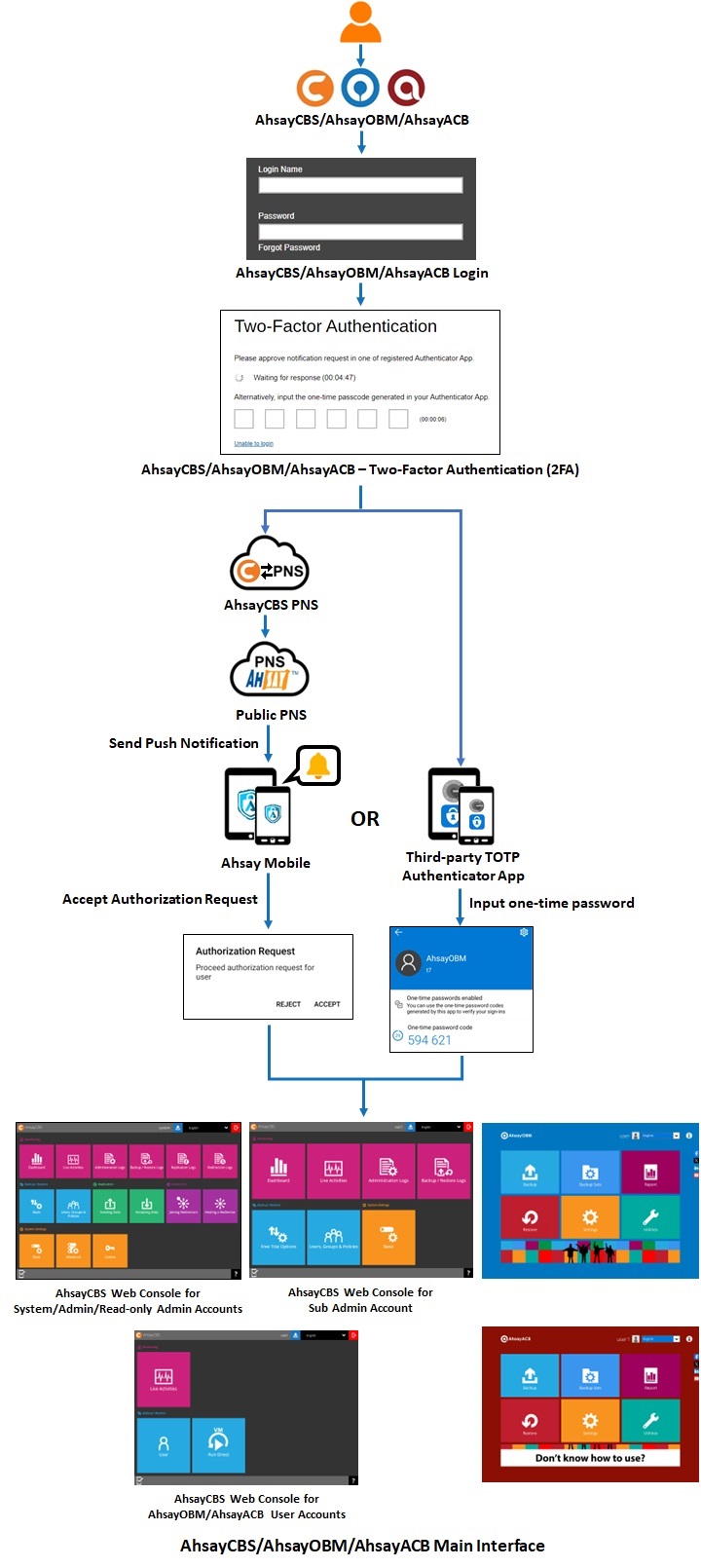
The system administrator can select which authenticator app the backup users must use to log in with 2FA. Here are the differences between Ahsay Mobile and third-party authenticator app:
| Ahsay Mobile | Third party authenticator app |
|---|---|
| Features | |
| Can be used for 2FA. | Can only be used for 2FA. |
| Can be used for mobile backup. | |
| Requirements | |
| AhsayCBS v10.1.0.0 or onwards must be installed. | |
| Must be registered with AhsayOBM and AhsayACB. AhsayOBM and AhsayACB must be connected to the internet. | |
| The mobile device must have a functioning camera for scanning of QR code to register 2FA. | |
| A mobile device with the latest version of Ahsay Mobile installed is available for 2FA. | A mobile device with a third-party authenticator app installed is available for 2FA. |
|
Ahsay Mobile must be installed on a supported Android or iOS mobile device.
|
A mobile device with a third-party authenticator app installed is available for 2FA. |
| The mobile device must have a valid mobile service and be able to receive SMS notifications. | |
| To use 2FA with https protocol, a valid SSL certificate from a trusted CA must be installed on AhsayCBS. Otherwise, you will have to use http instead which means all AhsayOBM/AhsayACB users with 2FA enabled will need to connect using http as well. | |
| The firewall on the AhsayCBS machine must be configured to allow outbound connections to pns.ahsay.com via port 80 or 443. Failure to do so will prevent you from logging in to AhsayCBS, AhsayOBM and AhsayACB using Push Notification feature. | |
| To use push notification for 2FA, the mobile device must have an internet connection. | |
| Ensure that Ahsay Mobile is connected to the same local WIFI network as the AhsayOBM/AhsayACB machine. Failure to do so will prevent Ahsay Mobile from performing backup/restore. | |
| Ensure to allow Notification on Ahsay Mobile for your mobile device. | |
| Limitations | |
| 2FA will not work in AhsayOBM and AhsayACB earlier than v8.5.0.0. | |
| For Replication, both sending and receiving are not covered. | |
| For Redirector, both hosting and joining are not covered. | |
| Not supported in AhsayOBR. | |
See table below showing supported system users, backup users and operating systems for 2FA:
| Supported Applications / Modules | |
|---|---|
| AhsayCBS | ✔ |
| - Replication (Accepting Data and Sending Data) | ✖ |
| - Redirection (Joining Redirectors and Hosting a Redirector) | ✖ |
| AhsayOBM | ✔ |
| AhsayACB | ✔ |
| Supported System Users | |
|---|---|
| Admin | ✔ |
| Sub-Admin | ✔ |
| Read-only Admin | ✔ |
| API User | ✔ |
| Read-only API User | ✔ |
| Supported Backup Users | |
|---|---|
| AhsayOBM / AhsayACB User (Paid) | ✔ |
| AhsayOBM / AhsayACB User (Trial) | ✔ |
| Supported Operating System | |
|---|---|
| Windows | ✔ |
| Mac | ✔ |
| Linux GUI | ✔ |
| Linux CLI | ✔ |
| FreeBSD CLI | ✔ |
| Synology DSM | ✔ |
| QNAP QTS | ✔ |
Set up Mobile Authentication
Switching on Mobile Authentication two-factor authentication support for AhsayCBS involves:
1st: Enabling Mobile Authentication in System Settings > Basic > Two-Factor Authentication (2FA)
2nd: Enabling Two-Factor Authentication of AhsayOBM/AhsayACB user accounts
Enable Mobile Authentication in AhsayCBS
There are two setup options for Mobile Authentication in AhsayCBS v10.1.0.0 and onwards:
- Set up using Ahsay Mobile as authenticator app
- Set up using Microsoft Authenticator, Google Authenticator or other third-party authenticator app
Set up Mobile Authentication Using Ahsay Mobile
-
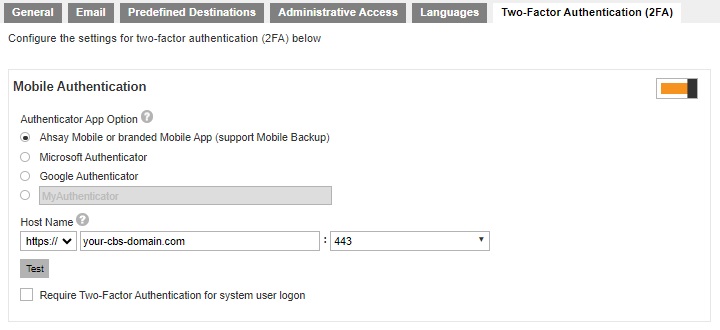
Switch on “Mobile Authentication”, by default it is switched off.
-
The following pop up message appears. Click OK to continue.
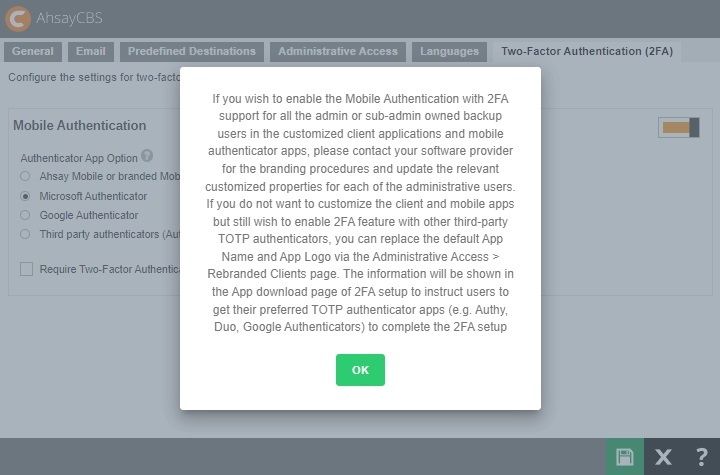 This pop up message will only appear if branded settings have been saved before enabling Mobile Authentication.
This pop up message will only appear if branded settings have been saved before enabling Mobile Authentication. -
Select the Authenticator App to be used for 2FA, in this case select Ahsay Mobile or branded Mobile App.
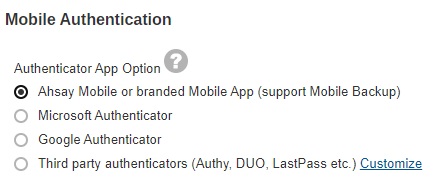
-
Register AhsayCBS Host Name details for 2FA:
- Select the type of protocol, whether http or https.
-
Enter the Host Name or external IP address of your AhsayCBS server.
The host name must be a FQDN (Fully Qualified Domain Name) which consists of the host name and domain name or an external IP address. -
Select the port used by AhsayCBS, for example 80 for http or 443 for https.
Example: https://your-cbs-domain.com

To use Two-Factor Authentication with https protocol, a valid SSL certificate from a trusted CA must be installed on AhsayCBS. Otherwise, you will have to use http instead which means all AhsayOBM/AhsayACB users with Two-Factor Authentication enabled will need to connect using http as well.
Another option would be to use other Authenticator App Option, i.e. Microsoft Authenticator or Google Authenticator, then there is no need to worry about SSL certificate and you may continue to use SSL with dummy certificate.
-
Click Test to verify. A confirmation message will be displayed once the verification is done.
-
Optional: Check the box if it is mandatory for system users to log in using two-factor authentication.

- Click Save to save.
Set up Mobile Authentication Using Third-Party Authenticator App
-
Switch on “Mobile Authentication”, by default it is switched off.

-
The following pop up message appears. Click OK to continue.

-
Select the Authenticator App to be used for 2FA, choices are:
- Microsoft Authenticator – will be used as the authenticator app for 2FA.
- Google Authenticator – will be used as the authenticator app for 2FA.
-
Third party authenticators – this option will allow end users to choose their preferred TOTP authenticator app for 2FA.
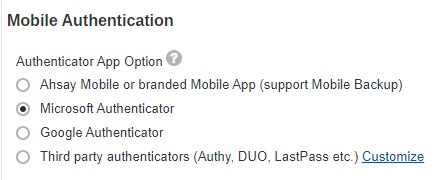
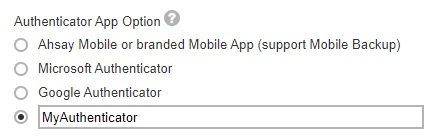
If Third party authenticators is selected, click Customizeto enter the name that will be displayed for the authenticator app on the “App Download and Device Pairing” screen”.
Example: MyAuthenticator
-
Optional: Check the box if it is mandatory for system users to log in using two-factor authentication.

- Click Save to save.
Although the 2FA setting has been setup on the AhsayCBS server, you have to enable 2FA for each AhsayCBS/AhsayOBM/AhsayACB user account before they can use it. For more information please refer to Enable Two-Factor Authentication of AhsayOBM/AhsayACB user accounts. For information on how to enable 2FA of AhsayCBS system user account, please refer to Enable two-factor authentication of system user.
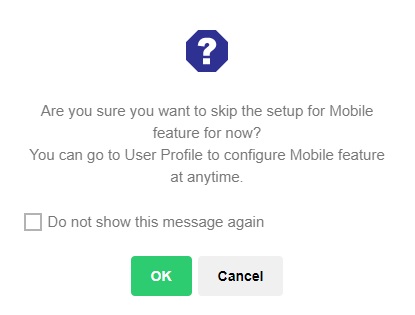
Once 2FA is enabled, upon login a message will be displayed where user can setup their 2FA.
This message will be displayed everytime the user logs in if there is no device paired for 2FA, not unless the “Do not show this message again” checkbox is ticked.
Enable Two-Factor Authentication of AhsayOBM/AhsayACB User Accounts
There are three ways to enable two-factor authentication of AhsayOBM/AhsayACB users:
-
The two-factor authentication can be enabled per individual AhsayOBM/AhsayACB user account in Backup / Restore > Users, Groups & Policies > Backup User > %backup user name% > User Profile > Authentication > Two-Factor Authentication.
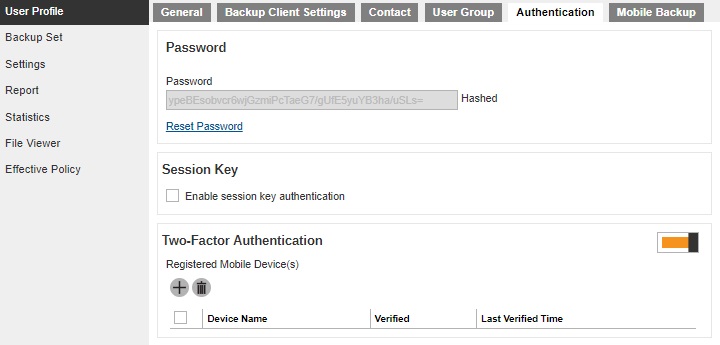
-
It can also be enabled for several AhsayOBM/AhsayACB user accounts at once in Backup / Restore > Users, Groups & Policies > Backup User.
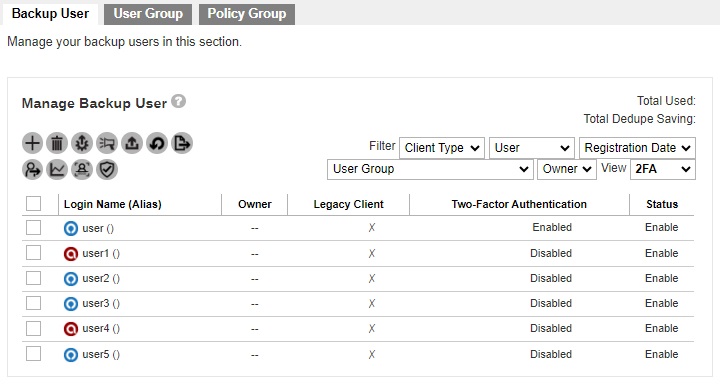
The “View” should be 2FA. Select the backup user that you want to enable 2FA. Then click the Enable / Disable Two-Factor Authentication button.
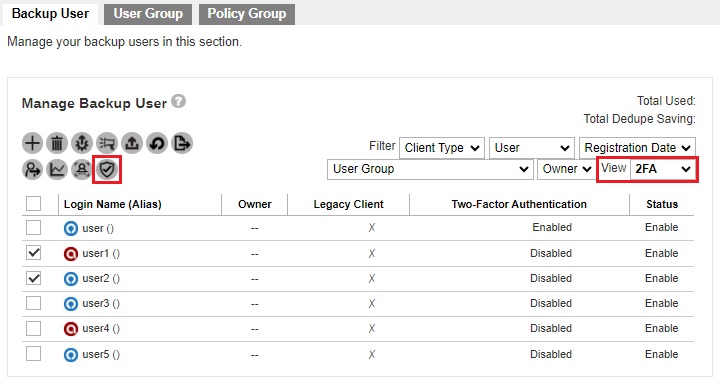
Click Enable to enable 2FA for the selected backup users.
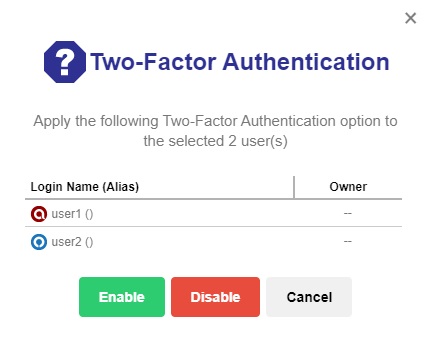
-
Or be enabled for all AhsayOBM/AhsayACB user accounts which can be done by enabling Require Two-Factor Authentication for user logon setting in Backup / Restore > Users, Groups & Policies > Policy Group > %policy name% > User Settings > Two-Factor Authentication.
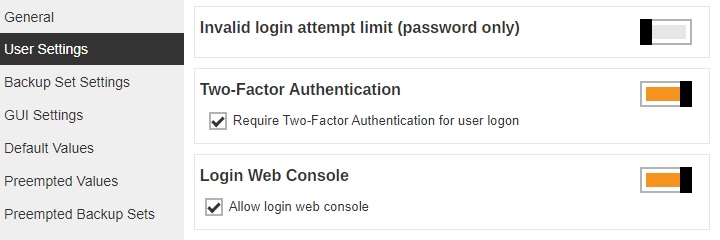
Once enabled, on the next log in for all AhsayOBM/AhsayACB v10.1.0.0 or above clients which support Mobile Authentication 2FA or AhsayCBS web console user login, will be required to register a mobile device for the new Mobile Authentication 2FA. Otherwise, they will not be allowed to proceed with the log in.
Here are examples of the next login in AhsayCBS web console after Require Two-Factor Authentication for user logon has been enabled.
Depending on the Authenticator App selected during setup of Mobile Authentication, the screen that will be displayed may be one of the four:
- Ahsay Mobile
- Microsoft Authenticator
- Google Authenticator
- Third-party authenticators
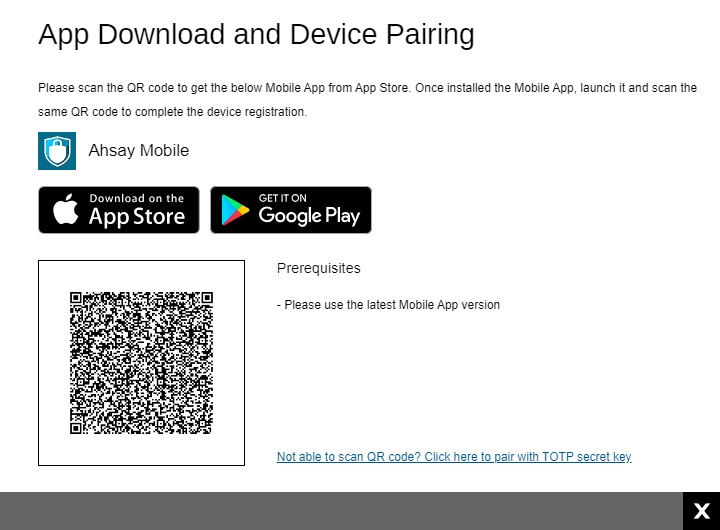
Ahsay Mobile
This is the default screen which has instructions to download Ahsay Mobile from the Apple App Store / Google Play Store. Scan the QR code to complete device pairing and finish the log in.
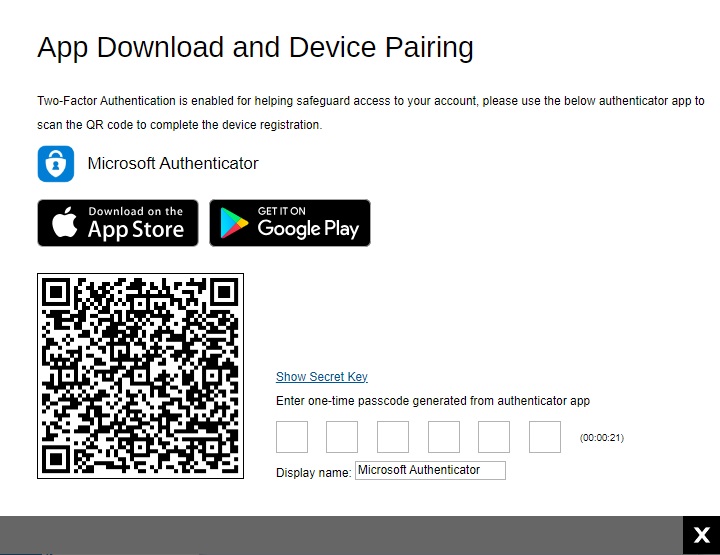
Microsoft Authenticator
If Microsoft Authenticator is selected, this will be the screen displayed. Scan the QR code using Microsoft Authenticator and enter the one-time passcode generated to finish the device pairing and log in.
Google Authenticator
If Google Authenticator is selected, this will be the screen displayed. Scan the QR code using Google Authenticator and enter the one-time passcode generated to finish the device pairing and log in.
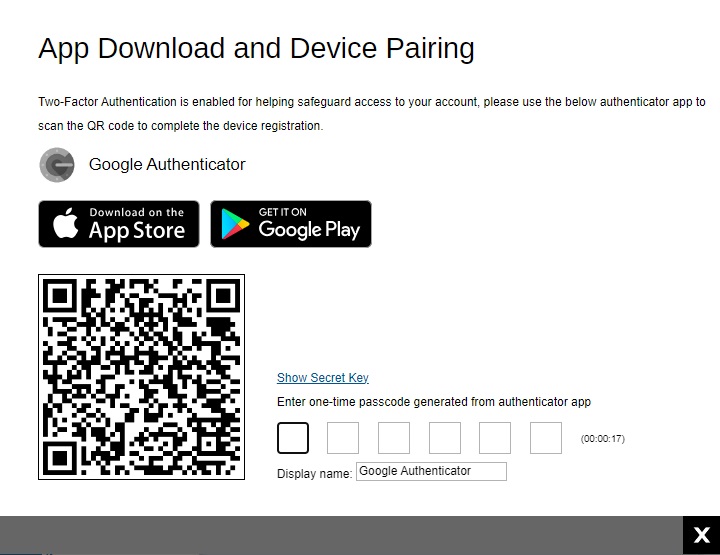
Third-party Authenticator
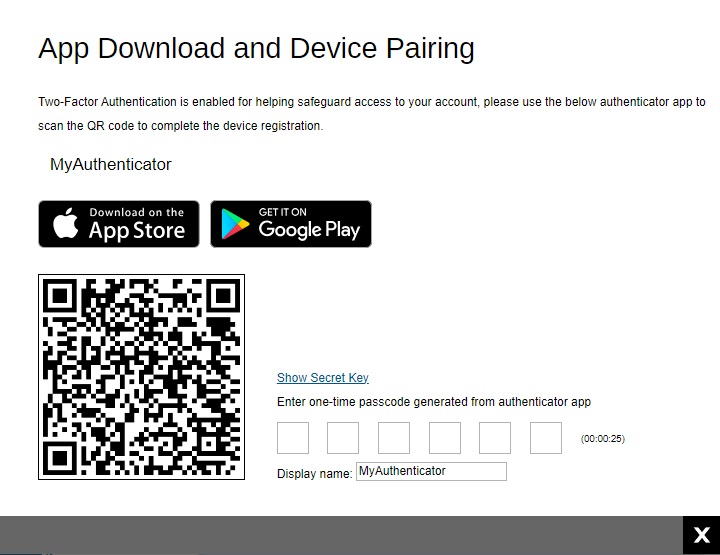
If Third party authenticators is selected, the name of the third party authenticator that will be displayed will vary. Here is an example using “MyAuthenticator” as the display name. Scan the QR code using your third party authenticator and enter the one-time passcode generated to finish the device pairing and log in.
Migrate Users From Twilio to Mobile Authentication
-
Switch on Mobile Authentication.
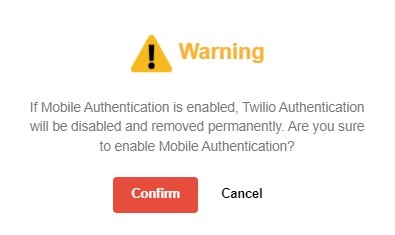
-
Click Confirm.
-
Twilio Credentials Verification is now deleted. Set up two-factor authentication and click Save to save.
-
Enable for your users by enabling the Require Two-Factor Authentication for user logon setting.

Once enabled, on the next log in for all AhsayOBM/AhsayACB v10.1.0.0 or above clients which support Mobile Authentication 2FA or AhsayCBS web console user login, will be required to register a mobile device for the new Mobile Authentication 2FA. Otherwise, they will not be allowed to proceed with the log in.
For examples of the default screen during next login in AhsayCBS web console after “Require Two-Factor Authentication for user logon” has been enabled, please refer to the previous section.
Twilio Credentials Verification
For users on AhsayCBS v8.3.0.30 until v8.3.6.x using Twilio, after upgrading to the latest AhsayCBS v10.1.0.0 or above, the existing Twilio Credentials setup will be migrated to the new version. So existing users can still continue using Twilio for two-factor authentication.
However, if Twilio has not been setup in the previous AhsayCBS version, setup of Twilio is desupported in AhsayCBS v10.1.0.0. Only modification of existing Twilio setting is allowed.
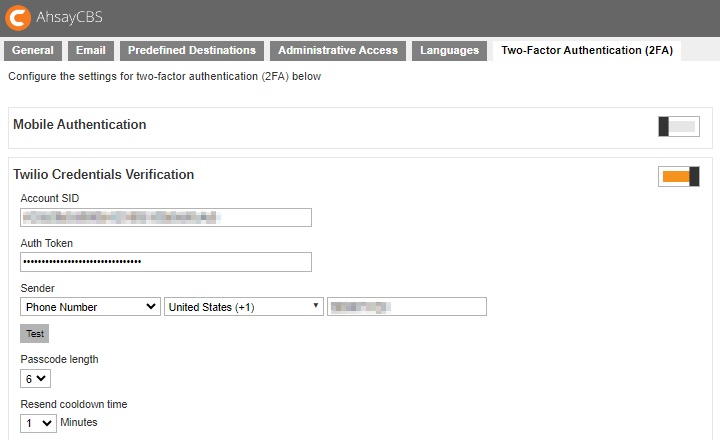
Modify Twilio Credentials
- Update the “Account SID”, “Auth Token” and “Sender” details, if needed.
- Click Test to verify.
-
Update the following: “Passcode length”, “Resend cooldown time”, “Expiry time”, “Consecutive invalid passcode attempts allowed” and “Consecutive resend allowed”, if needed.
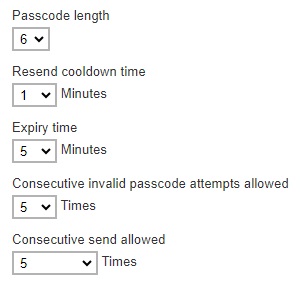
-
Check the box if you will allow legacy clients to skip SMS authentication. Legacy clients are AhsayOBM users who has an old version of AhsayOBM installed who upgraded to the latest version but has not run any backup yet. If this box is not checked, the user will be directed to the 2FA page.
- Click Save to save.
The “Allow legacy client to skip SMS authentication” box must be checked if you are using AhsayOBM/AhsayACB version older than 8.3.0.30 or else you will not be able to log in and your scheduled and continuous backups will not run. All functions requiring access and authentication to AhsayCBS will also not work. Like starting a manual backup from the System Tray in AhsayOBM/AhsayACB in Windows. Running AhsayOBM/AhsayACB batch files in Windows. Running AhsayOBM scripts in Linux/FreeBSD. Running AhsayOBM/AhsayACB scripts in MacOS. AhsayCBS server initiated backups on AhsayOBM/AhsayACB. And Auto Upgrade (AUA) on AhsayOBM/AhsayACB.
If you switch on Mobile Authentication or switch off Twilio Credentials Verification, Twilio Credentials Verification will be deleted from AhsayCBS permanently. It will not be possible to re-enable Twilio Credentials Verification at a later date.
Here are the warning messages you will receive:
-
Switch on Mobile Authentication

-
Switch off Twilio Credentials Verification

 AhsayCBS
AhsayCBS